BIG Changes to Cyber Essentials requirements
BIG Changes to Cyber Essentials requirements
Significant new changes to Cyber Essentials have been released by NCSC and IASME. These are the biggest changes to Cyber Essentials since it was introduced in 2014. I have been telegraphing many of these changes as personal wishes over the last year or so, and it seems that NCSC has gone above and beyond those wishes.
Changes TLDR
- Cloud services (Office365, Azure, AWS, Google GSuite, Slack, Zero, Zoom, Dropbox etc.) are now in scope (Portal services may also be in scope). Defiantly an area you will want to review.
- All servers (Physical/virtual/cloud) are now in scope (not a change for many, but now all are in scope regardless of internet access)
- Changes to password requirements
- Clarification of BYOD (not a change formalises what we have been working on for a while)
- Clarification of home working (not a change formalises what we have been working to for a while)
- Clarification to subset (how can we put out of scope sections of infrastructure)
- Updated question set and new better portal
- New tests for Plus
- All => CVSSv3 7 vulnerabilities are now in scope for Plus tests
- New Admin use test
- New Cloud MFA test
Scope Diagram should now make things more clear about what it is in scope. (Tip it’s probably in scope)
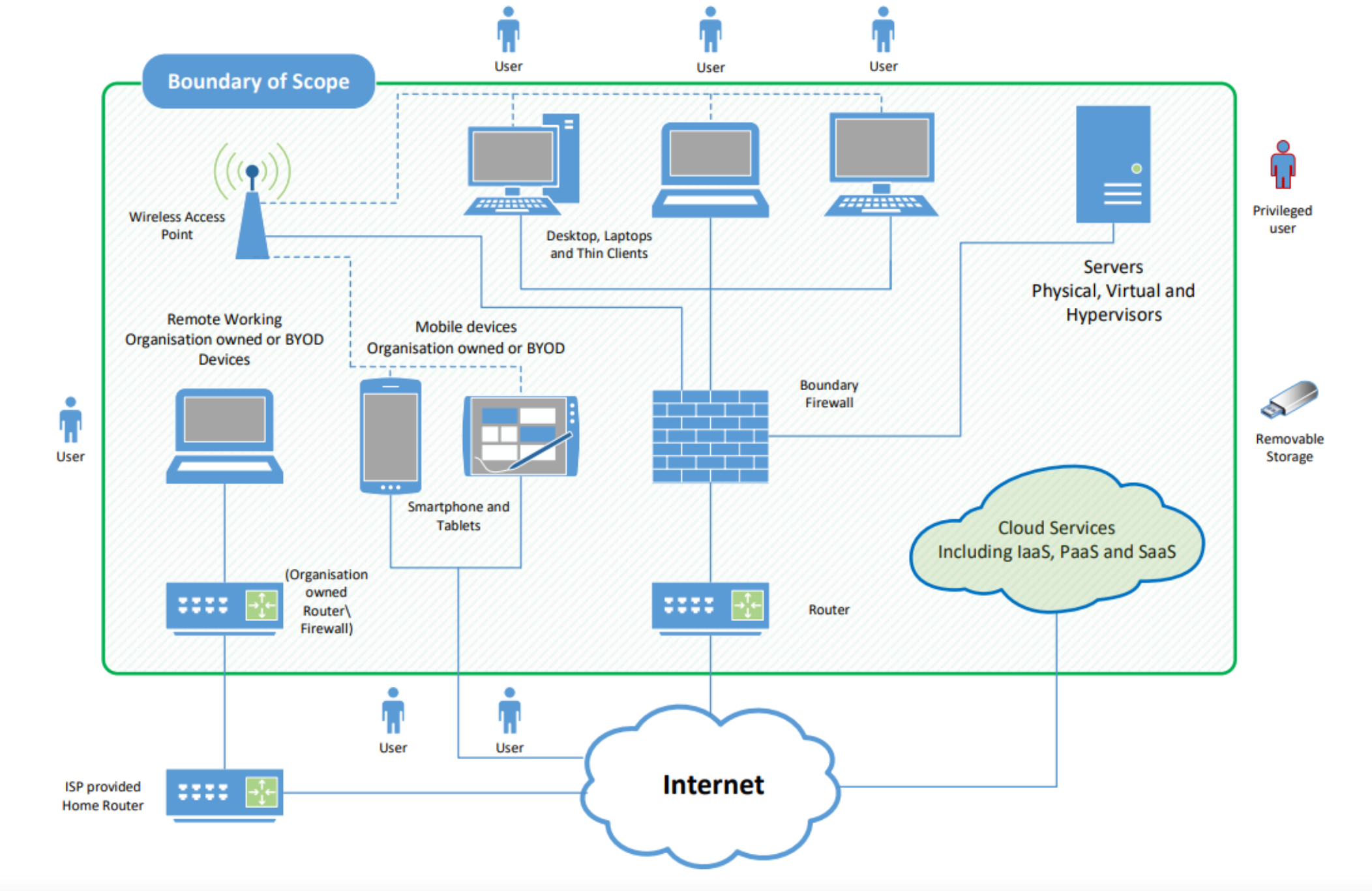
Cloud Service
Cloud Services are to be fully integrated into the scheme. The main change will be the addition of IaaS, PaaS and SaaS to the ‘Applies To’ each control. Each control requirement needs to be applied to Cloud Services Authentication in cloud services must always use MFA MFA to apply to all Users and Administrators. Definitions of Cloud services have been added for Infrastructure as a Service (AWS, Azure, Linode, Digital Ocean) (IaaS), Platform as a Service (Azure, Google App Engine, Magento) (PaS) and Software as a Service (SaaS) (Office 365, Gmail, Slack, Zoom, Dropbox, Xero)
| Requirement | IaaS | PaaS | SaaS |
|---|---|---|---|
| Firewalls | Applicant and Cloud Provider | Cloud Provider and sometimes also the Applicant | Cloud Provider |
| Secure Configuration | Applicant and Cloud Provider | Applicant and Cloud Provider | Applicant and Cloud Provider |
| User Access Control | Applicant | Applicant | Applicant |
| Malware Protection | Applicant and Cloud Provider | Cloud Provider and sometimes also the Applicant | Cloud Provider |
| Security Update management | Applicant and Cloud Provider | Applicant and Cloud Provider | Cloud Provider |
Passwords
Minimum 12 character password unless you are using MFA then you can have 8 (tip use 12) Password-based authentication Separate requirements on password-based authentication for services will be listed under User Access Controls.
- Protection against brute force.
- MFA applied, or deny list of common passwords, or 12 character passwords.
- use separate accounts to perform administrative activities only (no emailing, web browsing or other standard user activities that may expose administrative privileges to avoidable risks)
Device Locking
Device Locking included within Secure Configuration Control. The requirements on Device Locking are:
- Device Locking by Pin numbers, Biometrics and Passwords
- If credentials are solely to unlock a device, a minimum password or PIN length of at least 6 characters must be used The full password requirements in “user access control” must be applied when the credentials could also be used elsewhere.
Home Working (No real change, just clarification)
- Requirements for home working are now documented.
- All corporate or BYOD home working devices are in scope.
- ISP supplied Home routers are out of scope.
- Home users by default will rely on the Software Firewall
- A router supplied by the applicant’s company for use at home is in scope. The use of a corporate VPN transfers the boundary to the corporate firewall.
BYOD (No real change just clarification)
In addition to mobile or remote devices owned by the organisation, user-owned devices (laptops, chromebooks, smartphones, tablets, desktops) which access organisational data or services (email, office365 etc) are in scope. However, all mobile or remote devices used only for the purpose of:
- native voice applications,
- native text applications,
- multi-factor authentication applications are out of scope.
Please see more details on the updated requirement document v3 on the NCSC’s website
If you require support or consultancy with any of the above please get in touch
Stay safe, be well and make sure to wash your hands.